Why Targeted Bruteforcing is Your Secret Weapon for Content Discovery

Most penetration testers rely on generic (and even outdated) wordlists for content discovery, missing critical endpoints that could expose serious vulnerabilities. But there's a more sophisticated approach that dramatically improves your results: targeted bruteforcing.
The Problem with Traditional Content Discovery
Traditional content discovery often involves throwing massive generic wordlists at every target, regardless of the underlying technology stack. This approach has three major drawbacks:
- It wastes your valuable time scanning for irrelevant endpoints
- It increases your chances of missing out on technology-specific paths and files
- And lastly, it generates excessive noise that could've been avoided
Understanding Targeted Bruteforcing
Targeted bruteforcing takes a more intelligent approach by:
- First identifying the target's technology stack
- Then applying curated wordlists specific to those technologies
For example, when scanning an IIS server running ASP.NET, using an IIS-specific wordlist will uncover paths like:
- Administrative interfaces
- Known debug endpoints
- Configuration files that generic wordlists would likely miss.
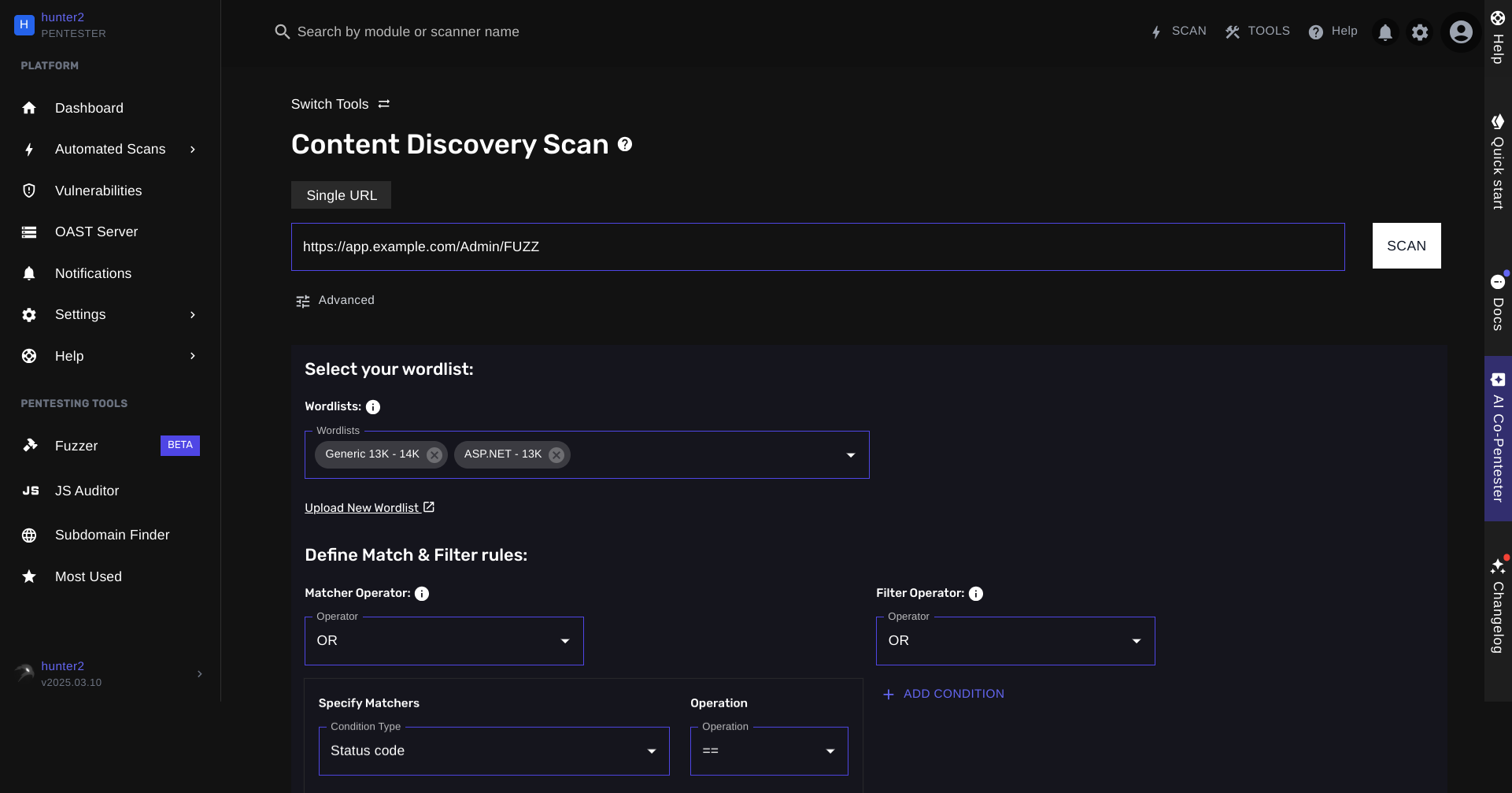
Introducing SPIDER X: Smart Content Discovery at Scale
SPIDER X brings targeted bruteforcing to the next level by combining:
- Intelligent technology detection
- Comprehensive headless crawling
- Smart wordlist selection (based on your target's technology stack)
- And other advanced URL discovery techniques
This multi-faceted approach helps you map complete attack surfaces much faster and much more accurately. It'll also find you hidden endpoints that other tools often miss.
Furthermore, this approach will also significantly reduce noise, something that your client might appreciate you for.
Real-World Impact
Targeted bruteforcing through SPIDER X typically reveals:
- Undocumented API endpoints
- Legacy admin interfaces
- Development artifacts
- Sensitive information exposure
- Potential security vulnerabilities
Getting Started with Targeted Bruteforcing
To leverage this approach effectively, always try to identify your target's technology stack prior to any bruteforcing. Afterward, select a custom wordlist that is specifically curated for the discovered technologies (such as PHP or ASP.NET).
Or you can deploy smart tools like SPIDER X on your next pentest to automate this entire process. All you have to do is specify a target to fuzz and click on "Scan".
Conclusion
While generic bruteforcing still has its place, targeted bruteforcing represents a more sophisticated and efficient approach to content discovery. By understanding your target's technology stack and using smart tools like SPIDER X, you can uncover critical endpoints that others miss.
Ready to try targeted bruteforcing? Start your 7-day free trial of SPIDER X today and discover what you've been missing!





