What Are Out-of-Band (OOB) Web Security Vulnerabilities?

Out-of-band web security vulnerabilities are generally harder to spot, especially in modern complex web applications. Most out-of-band security vulnerabilities even come with an elevated impact (such as SSRF) as they can provide unauthorized users with access to internal-only resources.
In this article, we will delve into what OOB web security vulnerabilities are, how they work, and how you can test for out-of-band (OOB) attacks.
What is an Out-of-Band (OOB) Attack?
Out-of-band (OOB) attacks refer to (web) security vulnerabilities that exploit the web application via an interaction between the vulnerable web app and an external system or service. Unlike traditional in-band attacks, which operate within the normal flow of data between a client and a server, OOB attacks involve sending data to an external entity, such as a remote server, email service, or DNS server.
The #1 Web App Pentesting Platform Favored by Pentesting Agencies Across the US
Set Up Your Private Out-of-Band (OOB) Server Today!It Supports Both DNS & HTTP Callbacks!
Try a Quick Demo →Common Examples of Out-of-Band (OOB) Attacks:
- Server-side request forgeries
- Blind SQL injections
- Blind XXE injections
- Blind command injections
- Blind cross-site scripting
How Out-of-Band (OOB) Attacks Work:
- Payload Injection. This is the phase where the malicious user or bad actor injects his/her specially crafted payload designed to invoke an unwanted action on the vulnerable web app, component or web service.
- External Communication. This is the step where the vulnerable component acknowledges the request of the malicious user and executes his/her payload resulting in invoking an external network request (this can be an HTTP, DNS, SMTP, etc, depending on the context).
- Data Exfiltration. The last phase is only possible when the vulnerable component is capable of processing the response data and returning it to the client (the malicious user).
How to Test for Out-of-Band (OOB) Attacks?
To test for out-of-band security vulnerabilities, you'd need an incoming request monitoring tool. A simple tool like our Out-of-Band (OOB) server that comes included by default with your account is sufficient.
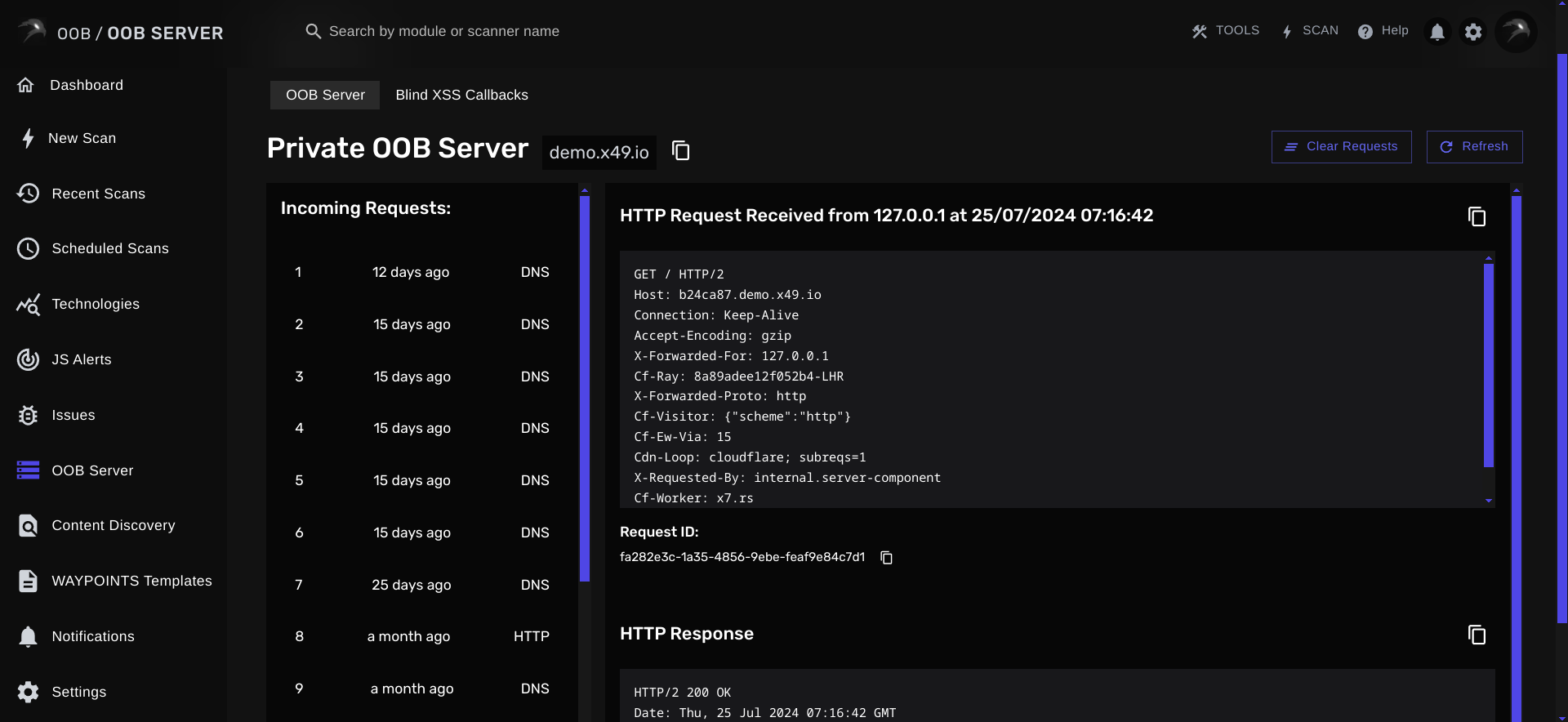
There are several other open-source and premium services available that are also capable of saving incoming network requests.
Once you have the server or tool set up and are ready to accept any incoming requests, you can use the hostname in your payloads. Read our SSRF exploitation article for more detailed examples of how to exploit out-of-band (OOB) attacks!
Conclusion
Out-of-band (OOB) web security vulnerabilities represent a significant threat to the security of web applications. As a pentester, you must understand how these attacks work and help your clients implement robust mitigation strategies so that they can better protect their systems and data from malicious actors. Staying up-to-date about the latest security trends (such as new CVEs) and making sure your clients adhere to best practices is essential for maintaining a strong security posture.





