The Only Content Discovery Tool You Need as a Penetration Tester
This article is intended for penetration testers who wish to discover more security vulnerabilities in web applications during their next pentesting engagement.

The difference between performing content discovery or skipping altogether can mean finding more critical security vulnerabilities at the end of the day or none at all. Penetration testers who spend more time and perform better content discovery on their web targets are often rewarded with cool vulnerabilities. And we all want to find cool bugs that we can tell our friends and colleagues about, no?
In this article, we will go over SPIDER X—the all-in-one content discovery tool that can be deployed on your web targets during your next pentesting engagement.
What is SPIDER X?
SPIDER X is an advanced all-in-one content discovery tool that is capable of performing several content discovery methods.
Its main goal? To return as many links, URLs and (query) parameters as possible.
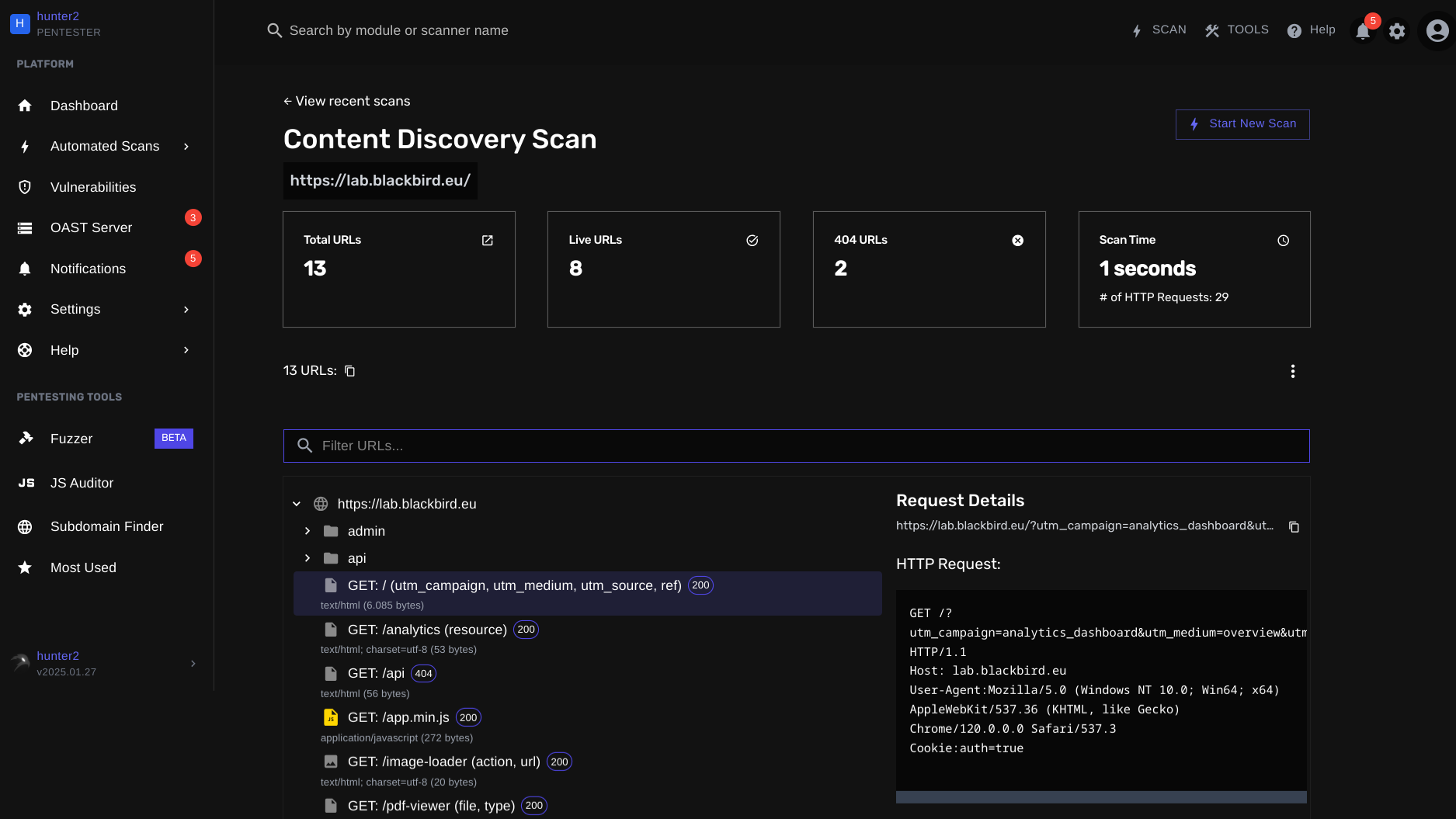
This is what makes it so advanced:
SPIDER X is a content discovery tool that always aims to return as many URLs, links and (query) parameters as possible on your target. It does so by utilizing several content discovery methods.
- Crawling and headless crawling
- Intercepting client-to-server & server-to-client HTTP requests
- JavaScript file parsing
- Enumerating client-side parameters (for DOM-based vulnerabilities)
- Performing targeted bruteforcing
- Querying external sources & internet archives (such as Wayback Machine)
- Parsing & enumerating app routes, endpoints and links in common server configuration files
DOM processing detection
Thanks to its native embedded browser support, it can perform various powerful tasks that would emulate a penetration tester's behavior. One of them is intercepting whenever a query parameter is processed by the DOM:
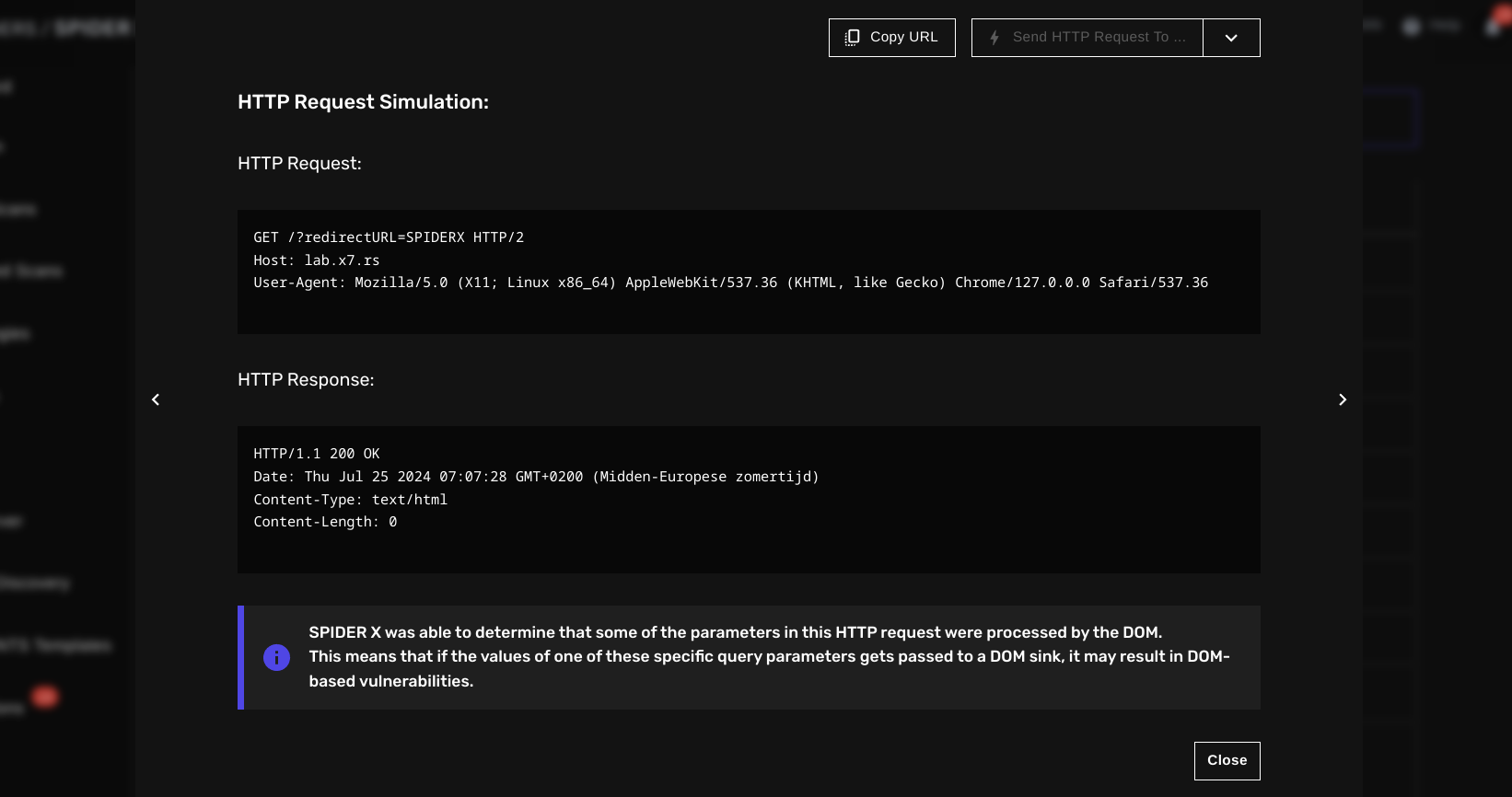
In the example above, SPIDER X was able to detect that the redirectURL query parameter was passed to a DOM sink, a perfect opportunity to test for DOM-based security vulnerabilities.
JavaScript file parsing
It is no secret that JavaScript files are often a goldmine for penetration testers as they contain several hard-coded secrets, from undisclosed APP routes & API endpoints to plain text credentials.
SPIDER X is of course capable of finding & parsing JavaScript files for you. It enables you to find more endpoints without having to go through and read the entire minified javascript file manually.
Targeted bruteforcing
Another interesting concept and what seems to be quite an effective way of performing content discovery is targeted bruteforcing.
SPIDER X is designed to fingerprint your target first and select a wordlist that matches the fingerprinted technologies before performing any bruteforcing. The results are way more accurate and it also prevents you from bruteforcing WordPress plugins on a server that runs on ASP.NET or has no WordPress installed at all.
We also have a default wordlist that acts as a fallback when no technologies are found. We frequently update our wordlists for you to keep up with the latest trends and attack techniques.
Try it out
We are confident that you will find substantially more URLs and links with SPIDER X than with other similar tools (we've tried). Give it a try on your next pentesting engagement.
Your first 7 days are free, and you also unlock a handful of other useful security tools that you can deploy during your pentest!





