Setting Up BLACKBIRD Burpsuite Integration: A Comprehensive Guide

In the ever-evolving landscape of web application security, having the right tools at your disposal can make all the difference. The BLACKBIRD Burpsuite Integration Extension bridges the gap between two powerful platforms, offering penetration testers an enhanced toolkit for identifying vulnerabilities with unprecedented efficiency.
In this guide, we'll walk you through the installation process, including setting up the Python standalone in Burpsuite, and provide a detailed overview of how to use this game-changing extension.
Installation: Getting Started with BLACKBIRD Burpsuite Integration
Prerequisites
Before we dive into the installation process, ensure you have the following:
- Burp Suite Community or Professional (latest version recommended)
- An active BLACKBIRD Web Application Pentesting Platform license with a valid API key
- Java Runtime Environment (JRE) 1.8 or later
Step 1: Download the Extension
- Navigate to the BLACKBIRD Burpsuite Integration releases page on GitHub.
- You can also download the extension through your dashboard by navigating to /burpsuite-extension
- Extract the contents into a local folder
Step 2: Set Up Python Standalone in Burpsuite
Burpsuite uses Jython, a Java implementation of Python, to run Python extensions. To ensure compatibility and smooth operation, we'll set up a Python standalone environment:
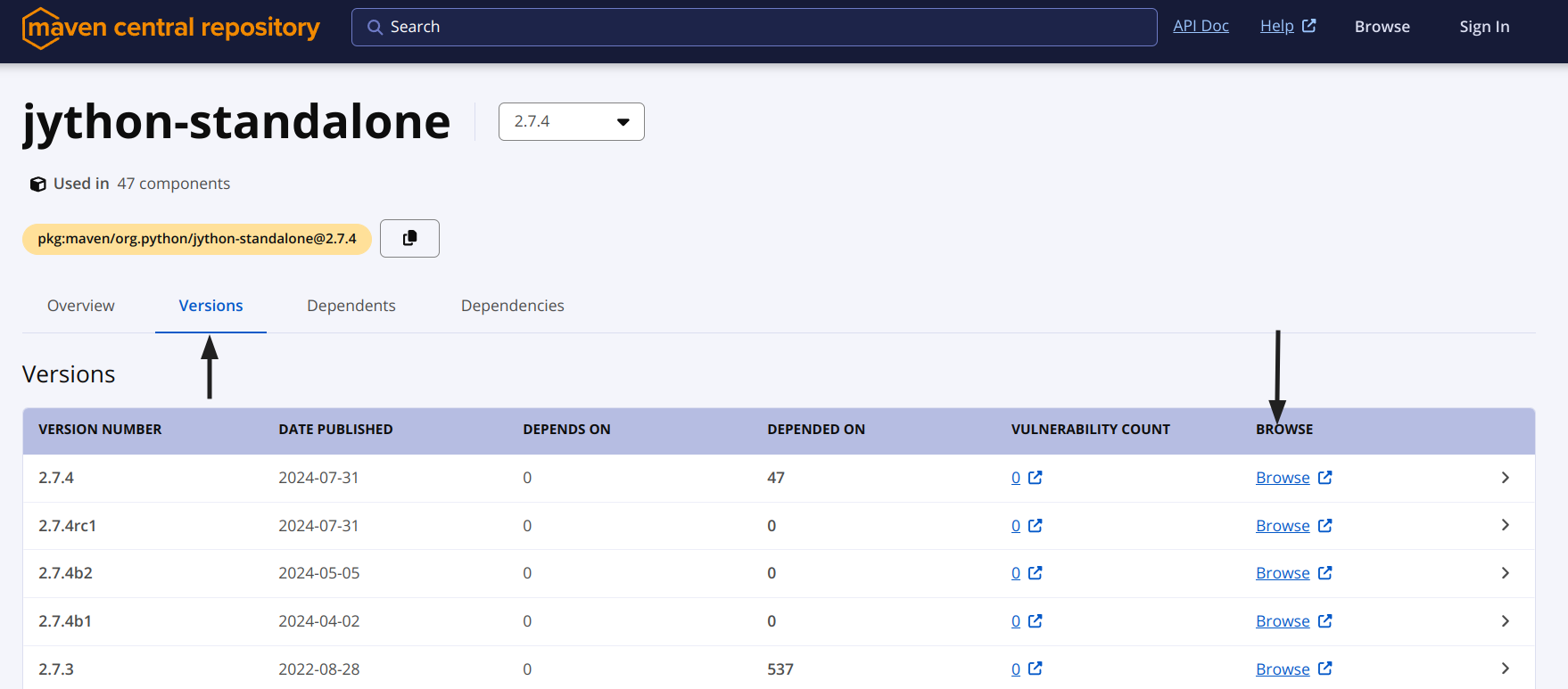
- Download Jython standalone JAR:
- Visit the Jython Downloads page.
- Click on "Jython Standalone JAR"
- This link will take you to the Maven Central Repository
- Open the "Versions" tab
- Click on "Browse" on the row with the latest version
- Download the latest Jython Standalone JAR file (e.g.,
jython-standalone-2.7.4.jar).
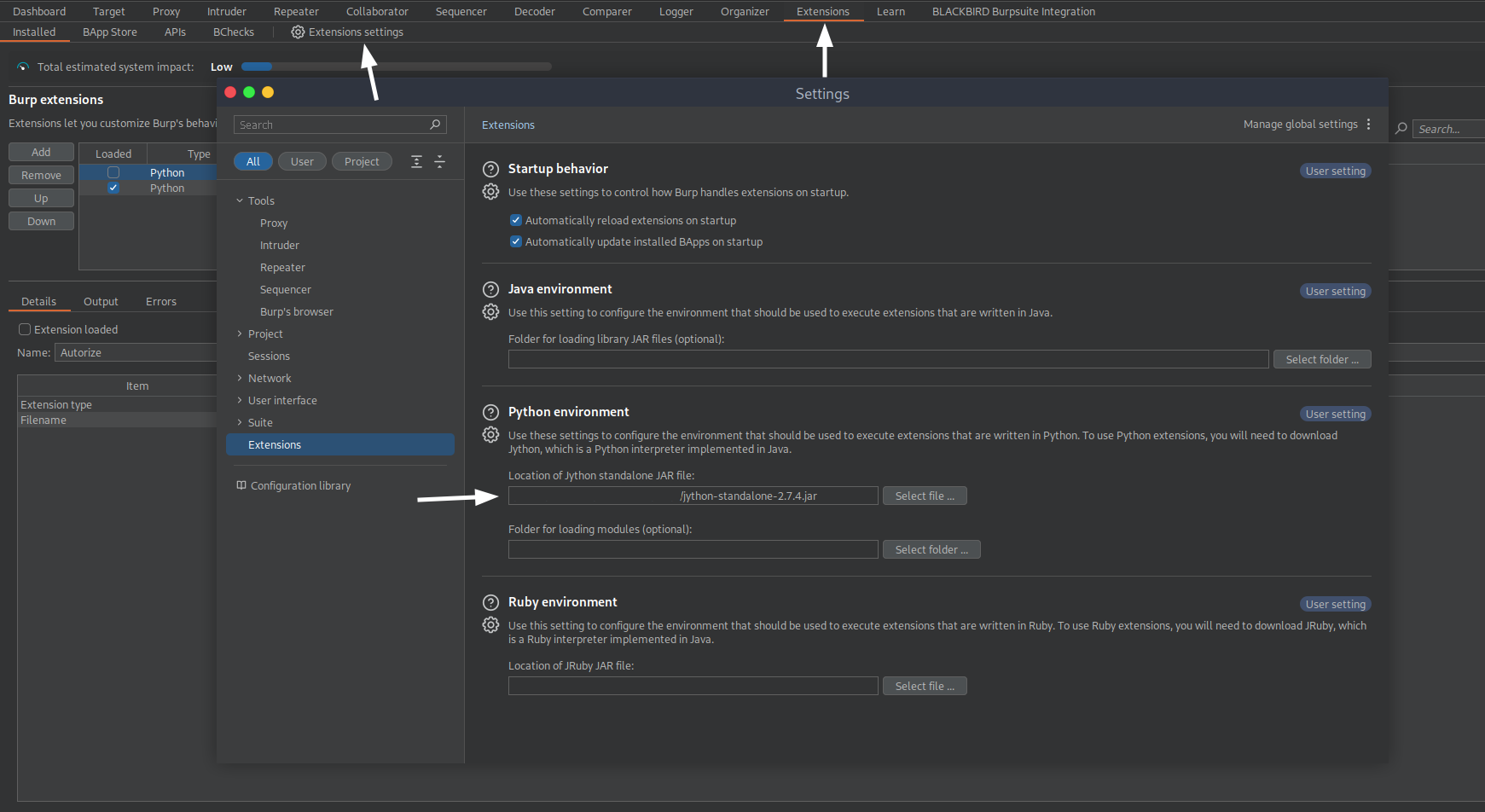
- Configure Burp Suite to use the Jython standalone:
- Open up Burpsuite.
- Go to the "Extensions" tab.
- Click on the "Extension settings" sub-tab.
- In the "Python Environment" section, select "Location of Jython standalone JAR file:".
- Click "Select file" and choose the Jython standalone JAR file you downloaded.
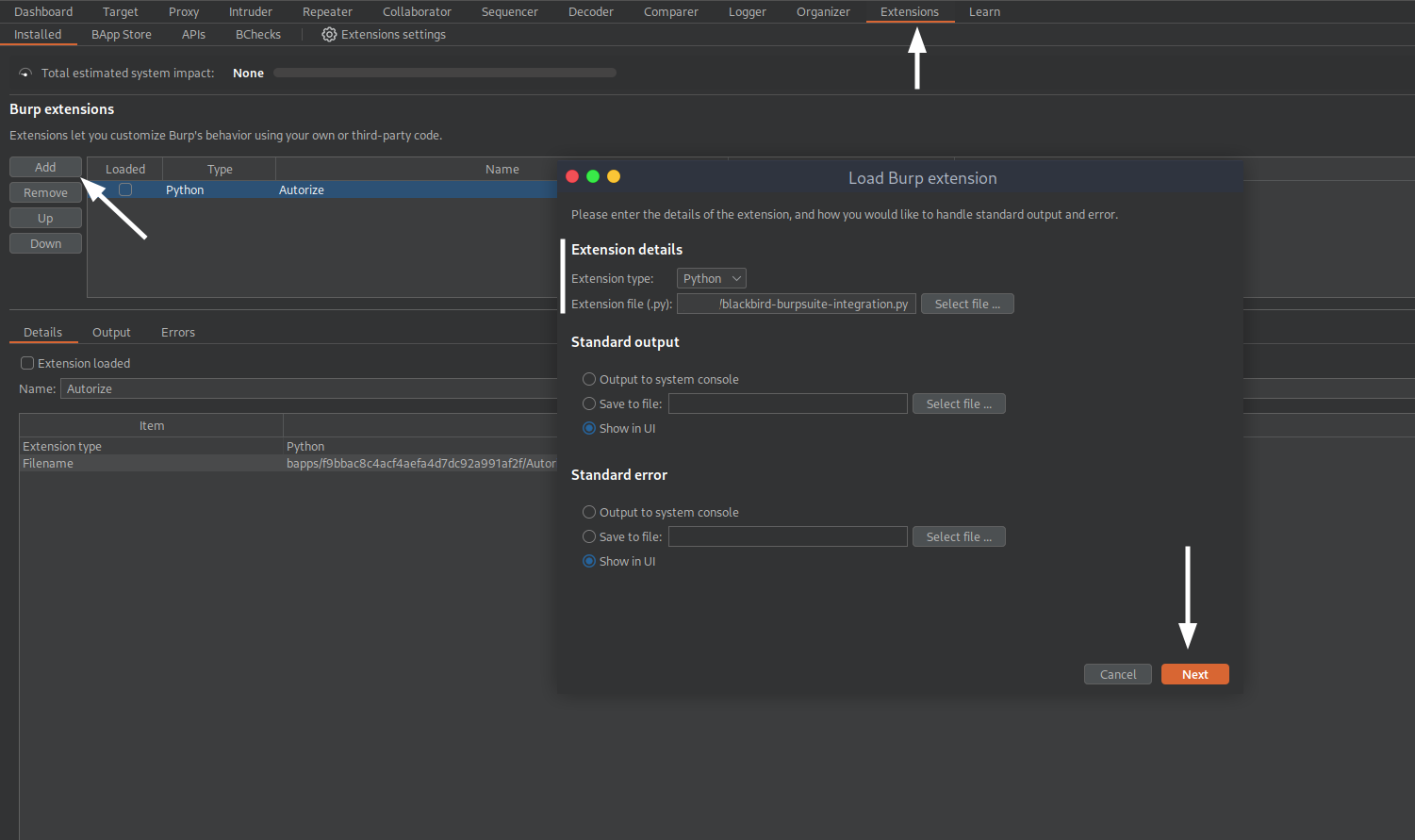
Step 3: Load the BLACKBIRD Extension
- In Burpsuite, go to the "Extensions" tab.
- Click on the "Add" button in the "Burp extensions" section.
- In the "Load Burp Extension" dialog:
- Set "Extension type" to "Python".
- Click "Select file (.py)" and choose the
blackbird-burpsuite-integration.pyfile you downloaded earlier.
- Click "Next" to load the extension.
- If successful, you should see "BLACKBIRD Burpsuite Integration" in the list of loaded extensions.
Step 4: Configure the Extension
- After installation, locate the new "BLACKBIRD Burpsuite Integration" tab in Burp Suite.
- Enter your BLACKBIRD API key in the designated "API Key" field.
- (Optional) Adjust the timeout and delay settings according to your preferences.
- Click "Save" to store your configuration.
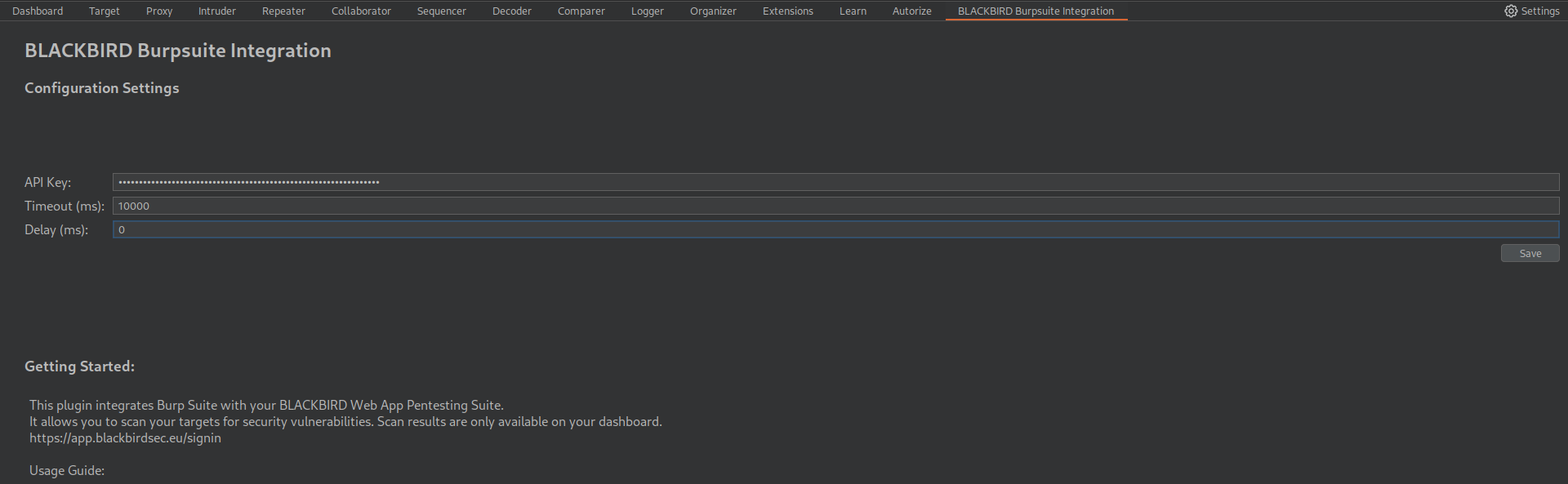
Congratulations! You've successfully installed and configured the BLACKBIRD Burpsuite Integration Extension.
Usage: Leveraging BLACKBIRD's Power within Burp Suite
Now that you have the extension set up, let's explore how to use it effectively:
Initiating Scans
- Navigate to any Burp Suite tool where you can interact with requests (e.g., Target, Proxy, Repeater).
- Right-click on a request you want to analyze.
- In the context menu, you'll find a list of "Scan URL for..." options provided by the BLACKBIRD extension:
- Command Injections
- SQL Injections
- Server-Side Request Forgery (SSRF)
- Local File Inclusion (LFI)
- Server-Side Template Injection (SSTI)
- Cross-Site Scripting (XSS)
- Open URL Redirects
- CORS Misconfigurations
- Select the type of scan you wish to perform.
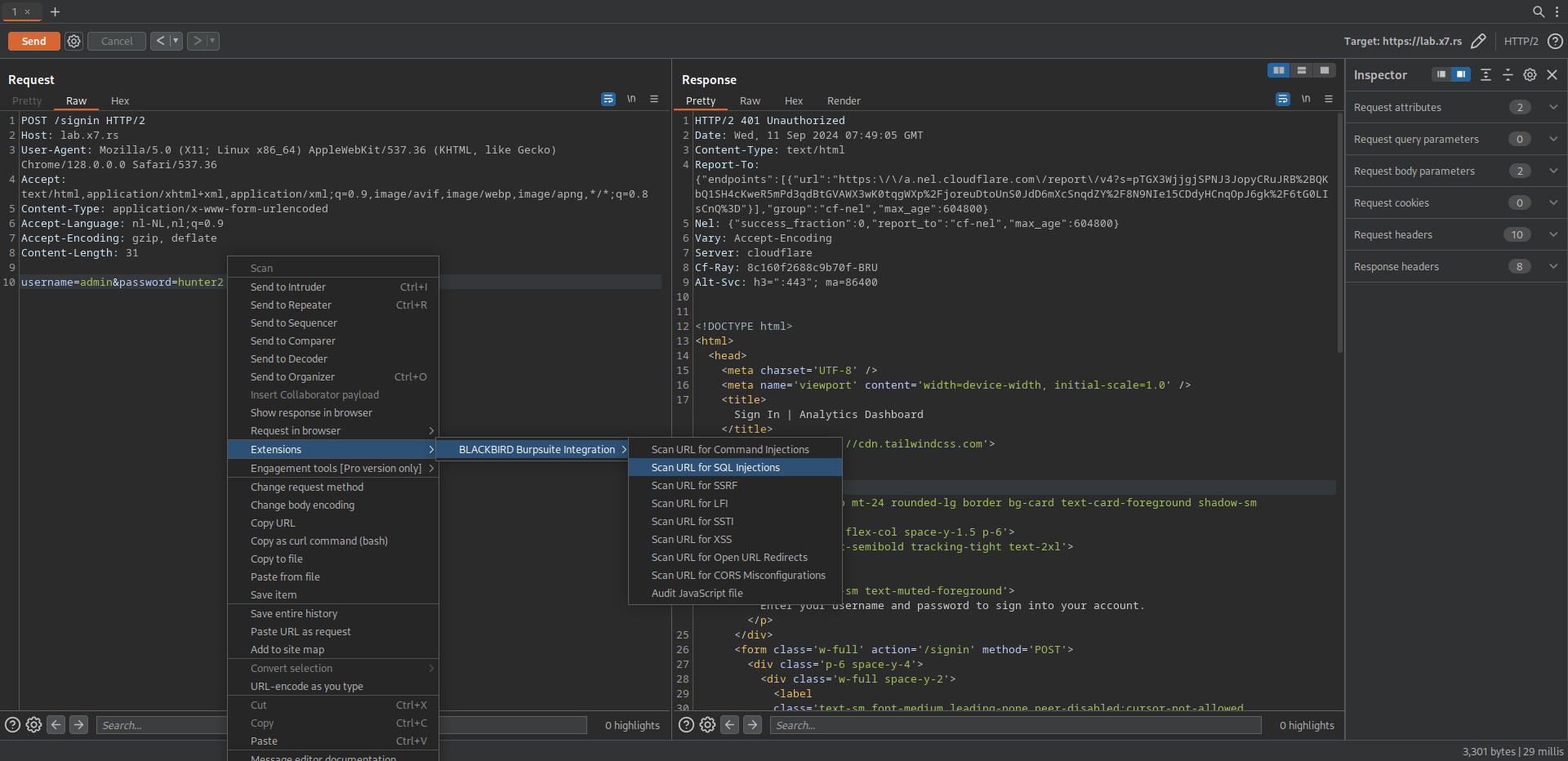
Auditing JavaScript Files
- Locate a JavaScript file within your target application.
- Right-click on the request for the JavaScript file.
- Select "Audit JavaScript file" from the BLACKBIRD extension options.
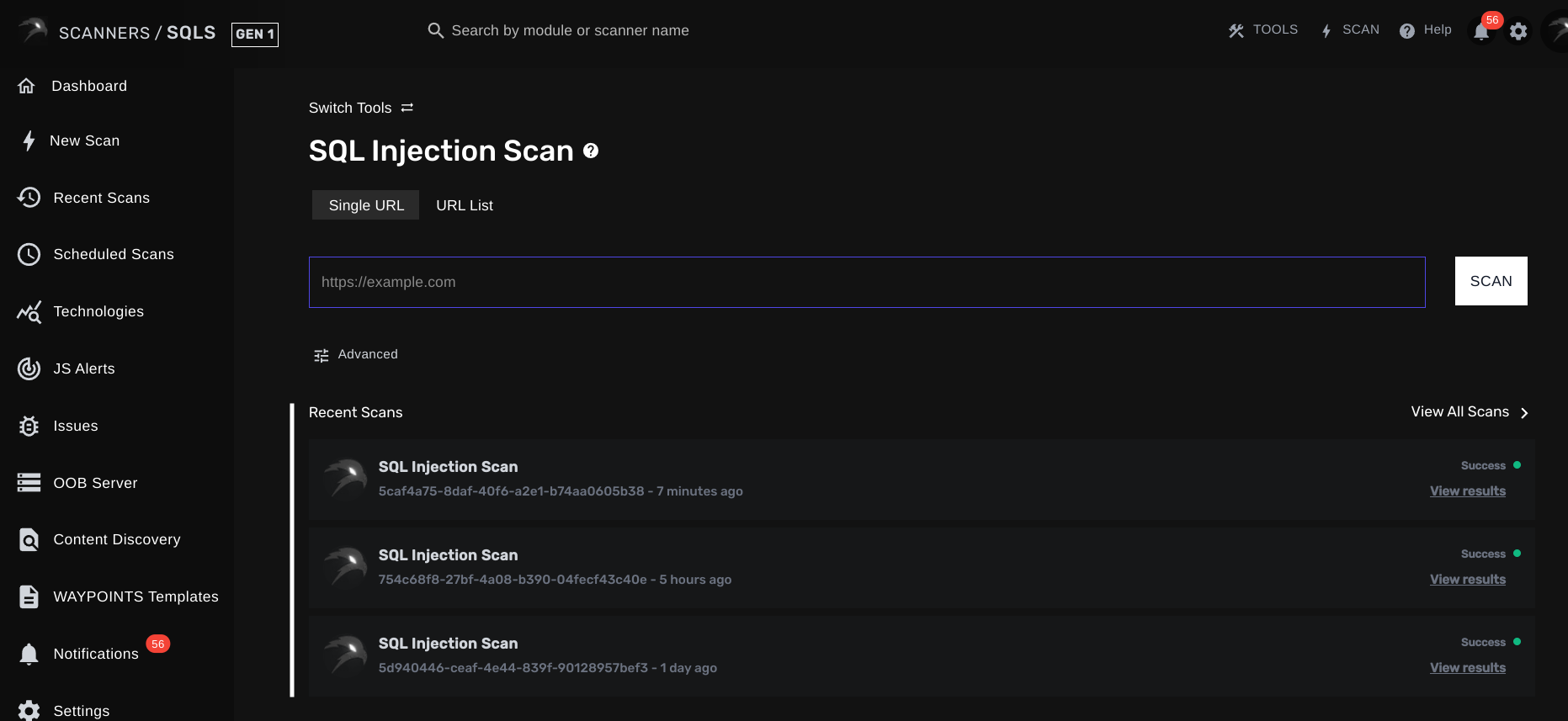
Viewing Scan Results
After initiating a scan:
- The extension will send the request to the BLACKBIRD API for analysis.
- Log in to your BLACKBIRD Web Application Pentesting dashboard at https://app.blackbirdsec.eu/signin.
- Navigate to the appropriate section to view your scan results (e.g. search for the scanner in the top search bar, your recent scans will appear immediately).
- If you've enabled notifications, you'll also receive alerts when vulnerabilities are discovered.
Best Practices
- Scope Your Scans: Always ensure you're scanning within the authorized scope of your penetration test.
- Rate Limiting: Be mindful of the rate at which you're sending requests. Adjust the delay settings in the extension configuration if needed.
- Validate Findings: While BLACKBIRD provides powerful automation, always manually verify critical findings.
- Stay Updated: Regularly check for updates to both Burp Suite and the BLACKBIRD extension to ensure you have the latest features and security patches.
Conclusion
The BLACKBIRD Burpsuite Integration Extension empowers penetration testers to streamline their workflow by combining the strengths of Burp Suite and BLACKBIRD's advanced scanning capabilities. By following this guide, you've not only learned how to install and configure the extension but also how to leverage its features effectively.
Remember, tools are only as good as the professionals wielding them. While this integration significantly enhances your capability to identify vulnerabilities, your expertise and judgment remain crucial in interpreting and acting upon the results.
New to BLACKBIRD Web App Pentesting Suite?
Is this the first time finding out about BLACKBIRD Web App Pentesting Suite? Try out a demo and discover what it can mean to you as a penetration tester!





