New Scan Mode to Scan a Single HTTP Request or Target For All Security Vulnerabilities

We're excited to announce a powerful new feature in the BLACKBIRD Web App Pentesting Suite: the ability to skip content discovery and proceed directly to vulnerability scanning. This addition offers penetration testers and security professionals a more targeted and efficient approach to identifying potential security weaknesses in specific web application components.
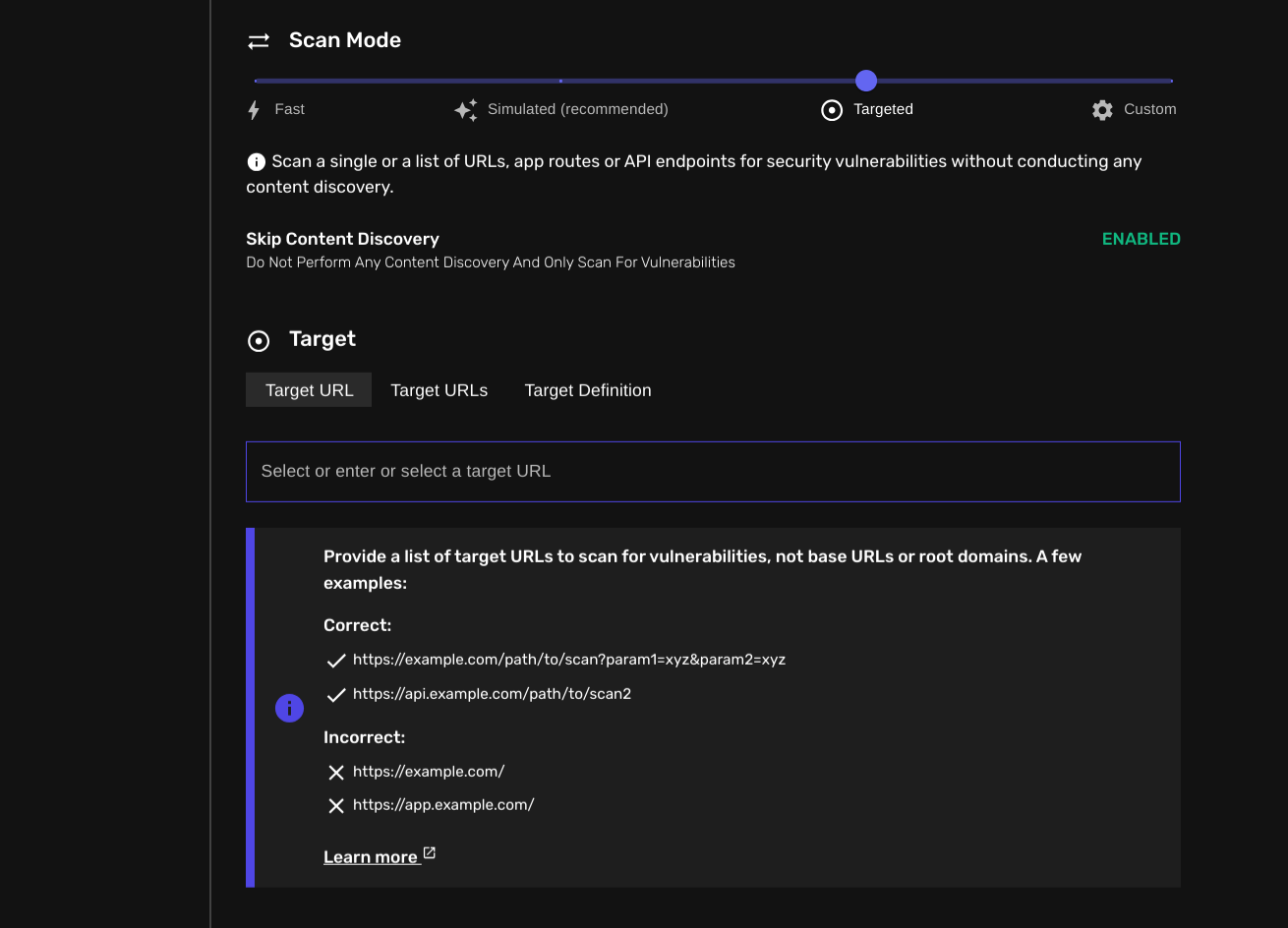
Previously, customers had to provide a root domain or target to scan it for security vulnerabilities. The content discovery scanner would be responsible for gathering all links, URLs, and parameters that could be further sent to each vulnerability scanner.
Now, you can skip that step altogether and just supply your app route, URL, API endpoint, or HTTP request and get it tested for thousands of security vulnerabilities with a single click.
What It Does
This new option allows users to bypass the content discovery phase and focus exclusively on scanning predefined URLs for vulnerabilities. It's designed for scenarios where you already know the exact endpoints you want to test, saving time and resources in the process.
Key Benefits
- Increased Efficiency: Concentrate your scans on known, high-priority targets without spending time on broad content discovery.
- Precision Testing: Perfect for assessing specific functionalities or newly added features in an application.
- Reduced Scan Time: By eliminating the content discovery phase, you can get results faster, especially in time-sensitive situations.
- Resource Optimization: Ideal for environments where minimal impact on the target system is crucial.
How to Use the New Feature
- Navigate to the scan configuration page in BLACKBIRD.
- Set the Scan Mode to "Targeted"
- Enter the specific URLs you want to scan under the "Target" section, including any necessary parameters or injection points.
This feature is also now available in your Burpsuite Integration extension!
Important Considerations
- Target URL Specificity: When using this feature, it's crucial to provide specific target URLs, not root domains. For example:
- Correct:
https://example.com/login.php?user=test - Incorrect:
https://example.com
- Correct:
- Include Parameters: For best results, include URLs with their associated parameters or potential injection points. This allows the scanners to perform more thorough and accurate vulnerability assessments.
- Use Cases: This feature is particularly useful for:
- Testing specific API endpoints
- Assessing newly implemented features
- Conducting focused security audits on known vulnerable areas
- Quick scans during the development process
Conclusion
The "Skip Content Discovery & Only Scan For Vulnerabilities" feature represents a significant enhancement to BLACKBIRD's flexibility and efficiency. By allowing customers to target specific URLs for vulnerability assessment, we're providing a powerful tool for more focused, rapid, and resource-efficient security testing.
We encourage our customers to try out this new capability and integrate it into their testing workflows where appropriate. As always, we welcome your feedback and look forward to hearing how this feature enhances your security assessment processes.
New to BLACKBIRD Web App Pentesting Suite?
Is this the first time finding out about BLACKBIRD Web App Pentesting Suite? Try out a demo and discover what it can mean to you as a penetration tester!





