New Fuzzing Capability For BLACKBIRD's Content Discovery Scanner

BLACKBIRD's all-in-one content discovery tool has just received a powerful update to its content discovery scanner, introducing advanced fuzzing capabilities that offer penetration testers more flexibility and precision in their assessments. This new feature significantly enhances the tool's ability to uncover hidden content and potential vulnerabilities within web applications.
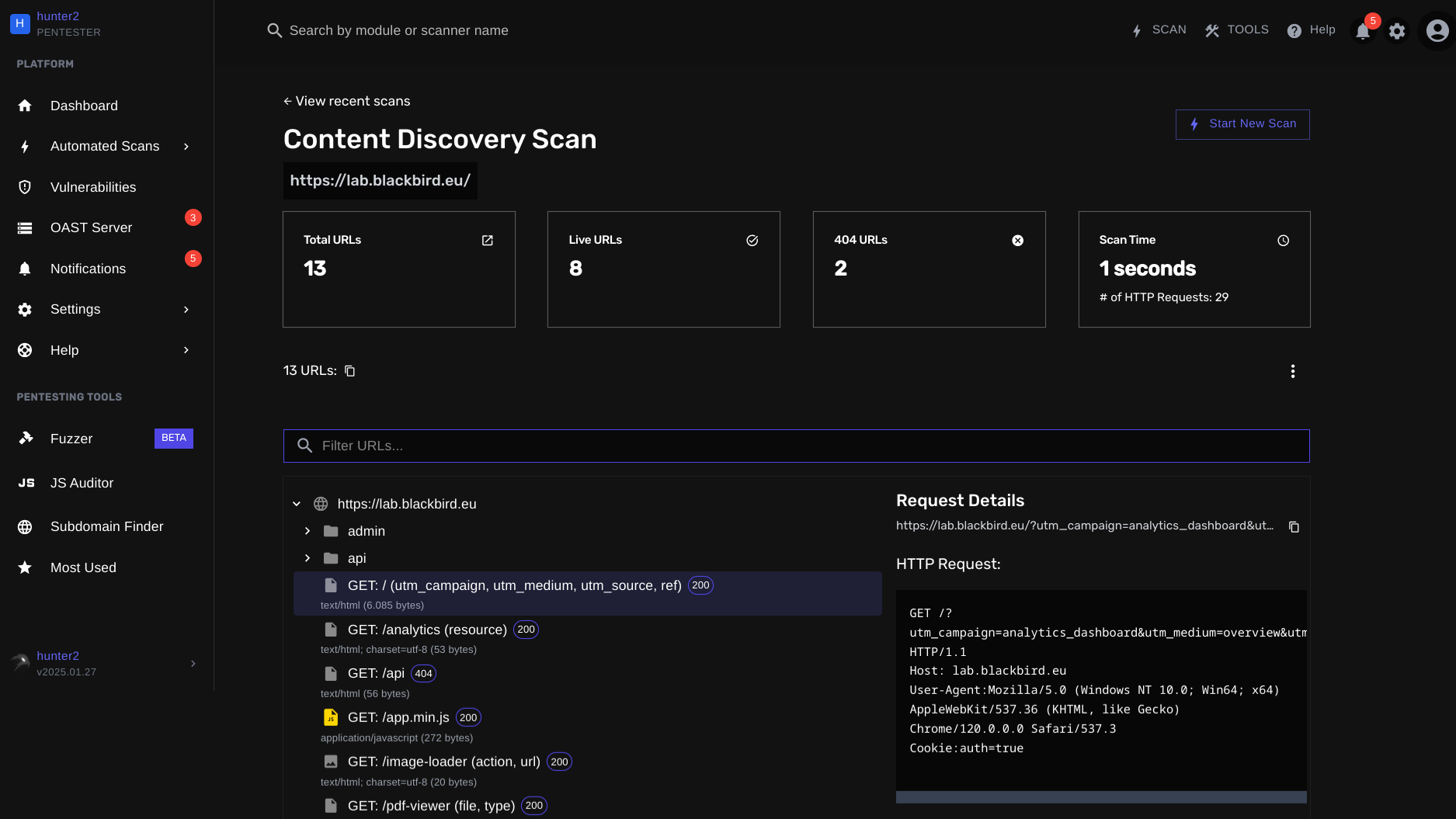
New Scanning Modes
The content discovery scanner now supports multiple scanning modes, allowing pentesters to tailor their approach based on specific testing requirements:
- DEFAULT: This mode performs a comprehensive scan, combining crawling and targeted bruteforcing for efficient & quick content discovery¹.
- ADVANCED: Builds upon the DEFAULT mode by incorporating headless crawling, ideal for more complex web applications.
- CRAWL: Focuses solely on rapid spidering of the target, perfect for quickly mapping out the structure and links within a website.
- HEADLESS_CRAWL: This mode solely performs headless crawling, useful for single-page application targets.
- FUZZER: The latest addition, designed for intensive directory and file enumeration. Supports the "FUZZ" keyword for precise targeting of specific subdirectories.
Each mode offers a unique combination of scanning techniques, with the new FUZZER mode being the highlight of this update.
The content discovery scanner is designed to leverage multiple content discovery techniques and is not limited solely to crawling & bruteforcing. For an in-depth exploration of its full capabilities, please refer to our detailed article.¹
FUZZER Mode: Targeted Bruteforcing Attacks
The FUZZER mode is designed for precise, targeted bruteforcing attacks. This mode focuses solely on directory and file enumeration without the additional overhead of crawling or spidering.
How to Use the New Fuzzing Feature
The FUZZER mode introduces a flexible way to specify targets for content discovery:
- Fuzzing the main path (default):
- Simply enter a valid URL, for example:
https://example.com/ - This will initiate fuzzing from the root directory
- Simply enter a valid URL, for example:
- Fuzzing a specific (sub)directory:
- Use the keyword "FUZZ" in the URL:
https://example.com/admin/FUZZ - This instructs the content discovery scanner to start bruteforcing from
https://example.com/admin/
- Use the keyword "FUZZ" in the URL:
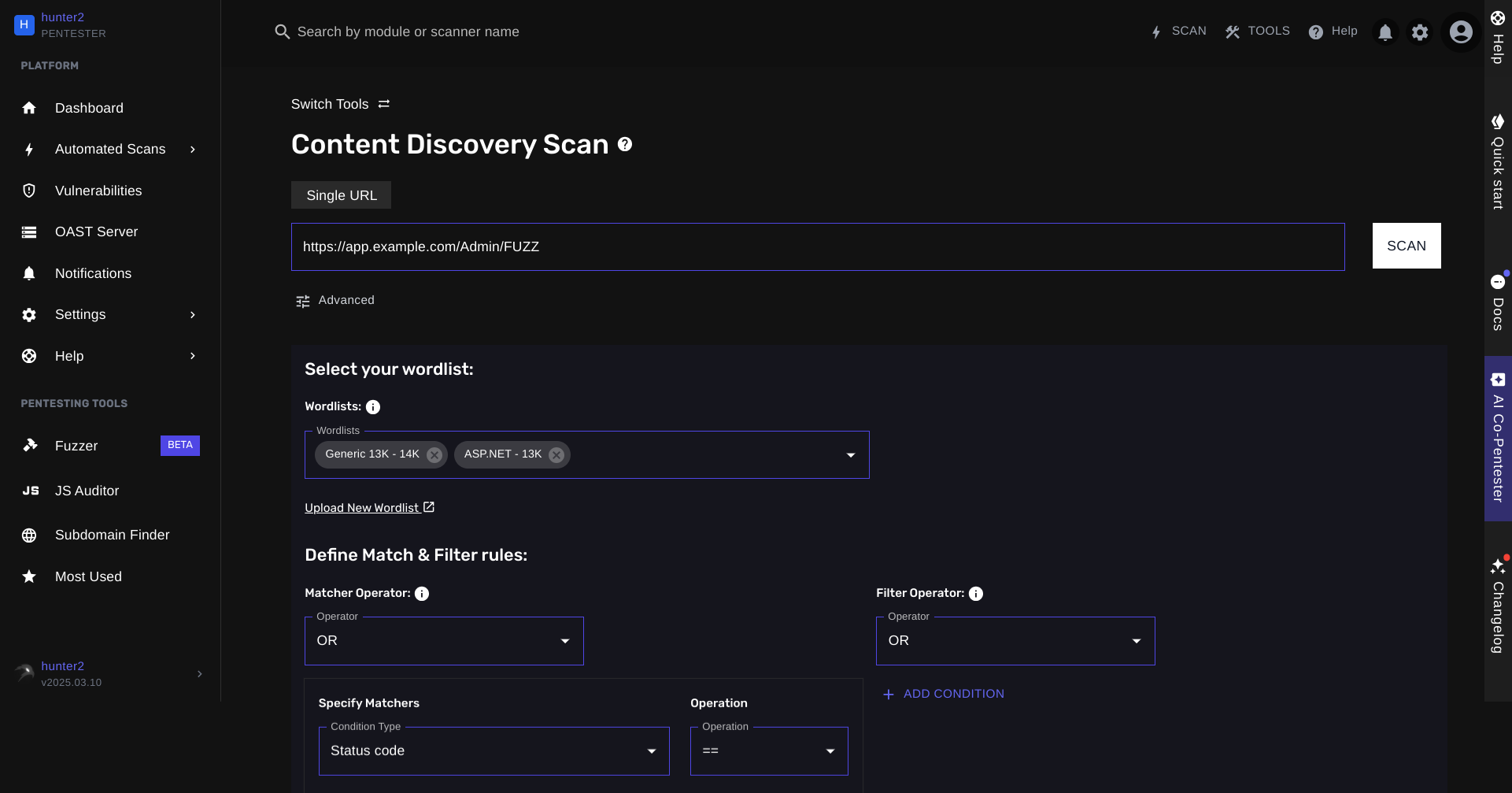
Step-by-Step Guide:
- Navigate to the Content Discovery Scan tool (from your dashboard, click on "Fuzzer" or from your module bar, search for "content discovery").
- Enter your target URL, (specify the "FUZZ" keyword if you want to specify a particular directory).
- Click on "Advanced" to reveal additional options and add any authentication data or rate-limiting instructions.
- Set the "Selected Mode" to "FUZZER".
- Review the scan details to confirm it matches your intended configuration.
- Click "SCAN" to initiate the fuzzing process.
Benefits of the New Fuzzing Feature
As a penetration tester, you've probably come across a scenario where you'd like to perform a quick bruteforcing attack on a target. This mode now allows you to do so from anywhere with a few clicks. Here are some other benefits that come with this new scan mode:
- Precision: Target-specific directories for thorough enumeration.
- Efficiency: Focus solely on bruteforcing without the overhead of other scanning techniques.
- Flexibility: Easily switch between fuzzing the main path or specific subdirectories.
- Resource Optimization: Ideal for situations where full crawling might be too time-consuming or resource-intensive.
Use Cases
- API Endpoint Discovery: Fuzz potential API paths to uncover undocumented endpoints.
- Hidden Admin Panels: Target common admin (or other areas for webmasters and managers) directory names to find hidden administrative interfaces.
- Backup File Detection: Fuzz for backup files or directories that might contain sensitive information.
- Custom Web Application Testing: When you have prior knowledge of an application's structure, use targeted fuzzing to dive deep into specific areas.
Conclusion
The addition of the FUZZER mode to BLACKBIRD's content discovery scanner represents a significant enhancement in web application penetration testing capabilities. By providing more granular control over the scanning process, penetration testers can now conduct more efficient and targeted assessments, potentially uncovering vulnerabilities that might have been missed by broader scanning approaches.
New to BLACKBIRD Web App Pentesting Suite?
Is this the first time finding out about BLACKBIRD Web App Pentesting Suite? Try out a demo and discover what it can mean to you as a penetration tester!





