How To Redirect Users Safely To Other Websites
You probably ever had to redirect your users from your website to another third-party's site that you do not control.
And because of that, you've added a function to your existing app route or endpoint that reads a (query) parameter, and redirects the user to the URL that was provided, and perhaps without any further validation.
This, by definition, is an Open URL Redirect vulnerability and can cause several consequences to your user's safety (from phishing to potential account takeovers).
In this post, we'll go over several ways on how you can easily avoid these and redirect your users safely.
Mitigation
Always ask yourself, is there a need to allow the user to get redirected to any kind of website from yours?
If this is not the case, a whitelist-based approach is the most effective solution. In practice, this means defining all whitelisted URLs and afterwards redirecting the user to end URL if the condition is allowed.
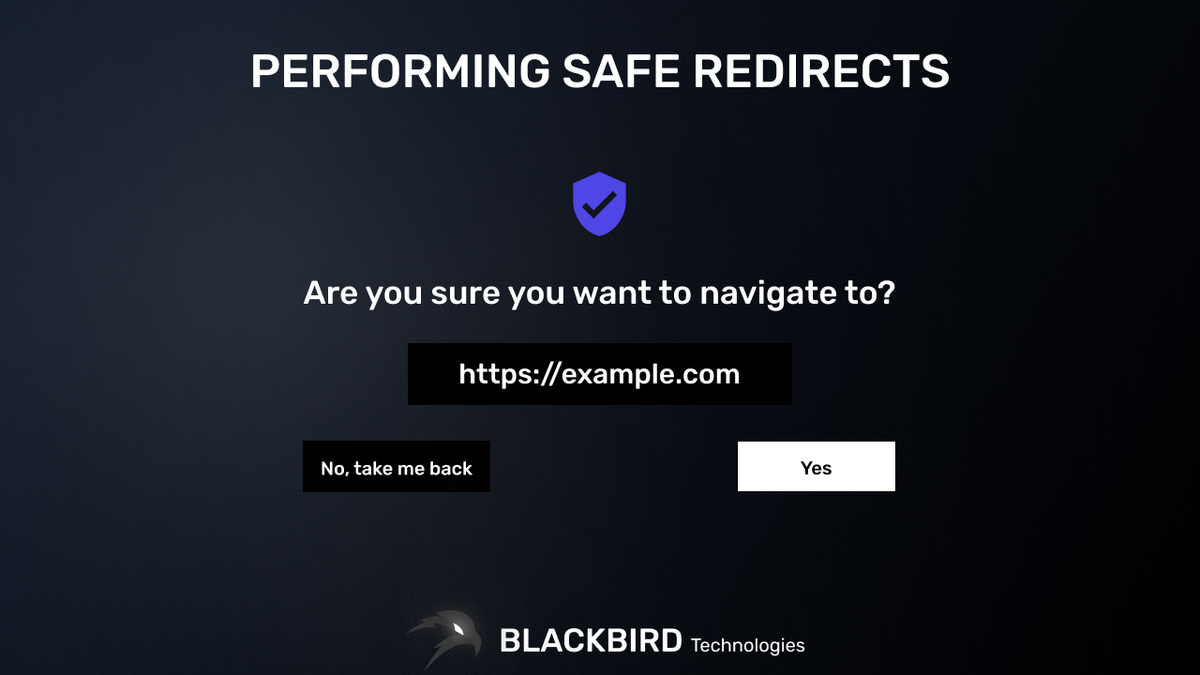
If you do need to redirect users to another website that you do not control (think about a blogging platform or a public forum), the safest way to do so is prompting the user for confirmation before redirecting.
This can be a separate page or view that the user gets to see before the redirect takes place.
This makes sure that:
- The user is well-aware of a redirect.
- The user can view the full URL or link that he/she is about to visit.
Example:
This is beyond the scope of this post but you can read more about it on our blog.
Scan For Open URL Redirect Vulnerabilities on Your List of Targets
Check Out the Most Powerful Web App Pentesting Suite Made by Pentesters for Pentesters!
Try a Quick Demo →




