Hidden JavaScript Vulnerabilities That Most Pentesters Miss (And How JSAuditor Finds Them)

JavaScript files are goldmines for penetration testers. But with modern applications containing hundreds of chunked and minified JavaScript files, even the most skilled security professionals can't manually review every line of code. And that often goes paired with missing critical security vulnerabilities.
That's where JSAuditor, a power lightweight javascript analysis tool specifically designed for penetration testers comes into play.
This article heavily promotes our web application pentesting suite, specifically JSAuditor, one of our pentesting tools. If you'd like to skip reading this article and try a quick demo instead, click here.
Vulnerabilities Hidden Deep Inside JavaScript Files
Modern web applications heavily rely on JavaScript, with frontend frameworks like React and Angular pushing more logic to the client side. This shift has created new attack surfaces, such as hard-coded credentials, references to internal or exposed assets for development purposes and even source map files that allow you to recreate the entire folder structure of the application project.
We've tested several open-source JavaScript auditing tools and most of them unfortunately didn't meet our expectations. Because the challenge isn't just finding these vulnerabilities, links and all other interesting data in JavaScript files, it's also about finding them efficiently within massive codebases while making sure nothing is left unchecked.
That's where JSAuditor comes into play:
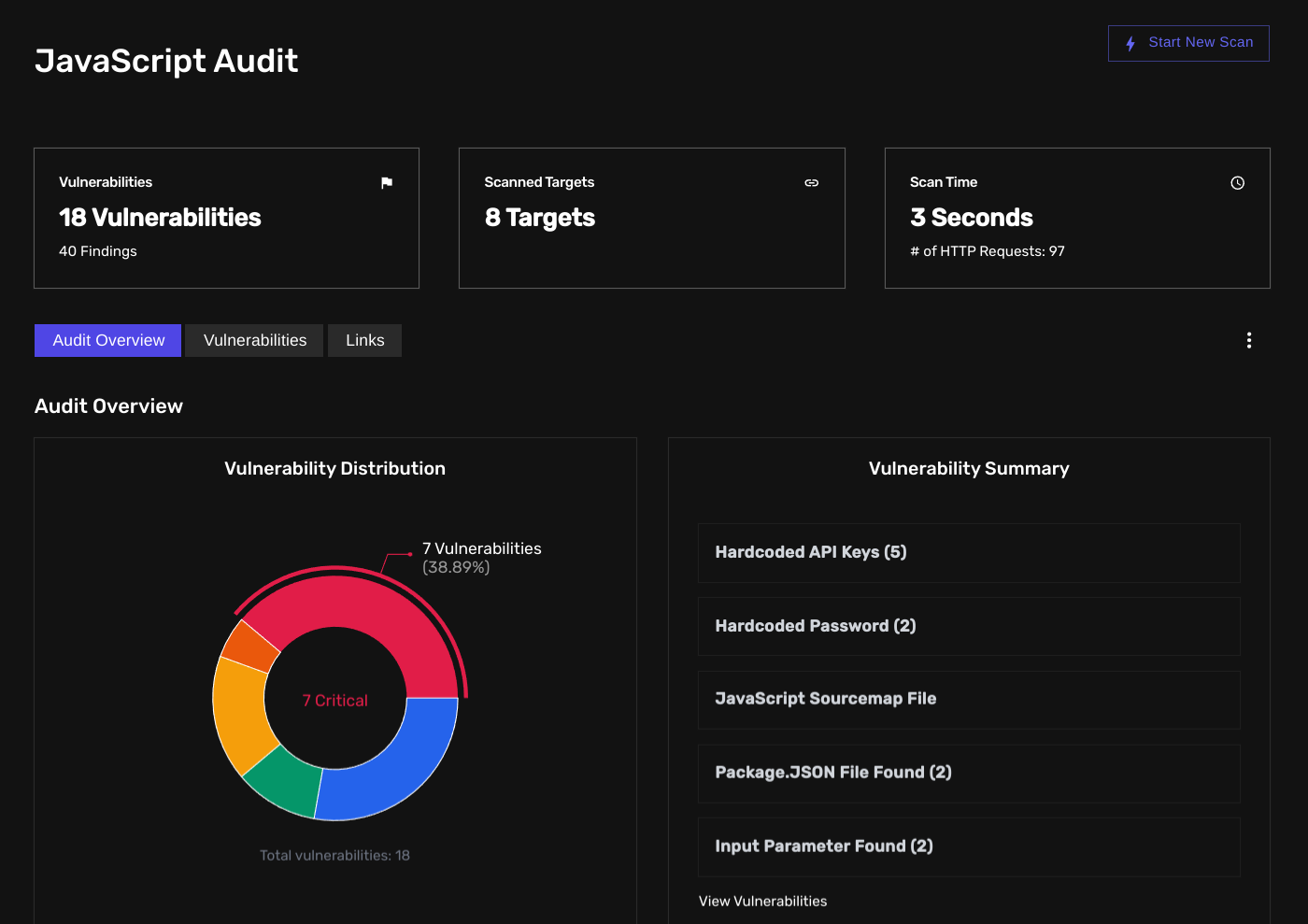
JSAuditor: A Lightweight JavaScript Pentesting Tool
JSAuditor is a lightweight JavaScript auditing tool that performs deep analysis of JavaScript files. It can help you find all sorts of issues commonly found in JavaScript files such as:
- Disclosed & hard-coded secrets (such as API keys and credentials)
- URLs and other referenced endpoints (app routes & API endpoints)
- Query parameters
- JavaScript source map files
- Potential dependency confusion vulnerabilities
- Disclosed package.json files
- NPM packages (and their associated version numbers)
Unlimited Vulnerability Scans For 7 Days
We've wanted to make it easy for new pentesters to try out BLACKBIRD Pentesting Suite: for 7 days, you can launch unlimited vulnerability scans and try all the tools out that the entire pentesting suite features.
Our goal is to have you try out BLACKBIRD. With that, you can weigh in BLACKBIRD is something for you, and we gain your trust. Fair enough?
Start your free trial today and experience the full power of automated JavaScript security analysis.





